Are you looking for a new way to improve security to connect to your VMs in Azure? You should check out the feature Azure Bastion.
In the past, to secure RDP and SSH connectivity to your Azure Virtual Machines, you probably had to use a jump box where people connect in order to access the other VMs.
Of course a jump box improves the security on your access but it introduces some gaps that Azure Bastion addresses.
Azure Bastion overview
First of, Azure Bastion is a Platform as a Service service that provides a secure RDP and SSH connectivity to shield your Azure Virtual Machines.
Implementing Azure Bastion allow access to all VMs within a virtual network through a single hardened access point, the AzureBastionSubnet.
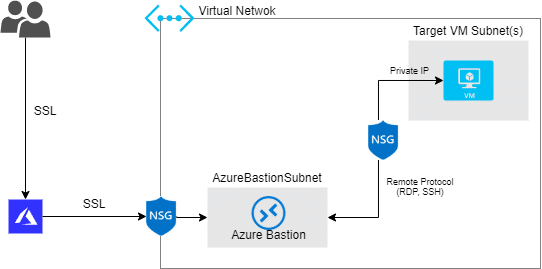
And as you can imagine, the connection to your VM will now happen via Azure Portal which connects to the Azure Bastion service using its public IP and loads your VM directly on your browser.
Cost
To enjoy the benefits of Azure Bastion, you will have an additional cost to your subscription
US$0.19/hour (~ US$138.70/month per Azure Bastion)
And, you also have an Outbound Data Transfer cost, but prices might vary depending on the usage. However, the first 5GB/month are free.
Requirements
To provision Azure Bastion
- Bastion is available in most Azure regions but on these
- Canada East
- France South
- Italy North
- Switzerland West
- Germany West Central
- Germany North
- Germany Northeast
- Germany Central
- UAE North
- South India
- China East
- China East 2
- China North 2
- Australia Central
- South Africa East
- Your Virtual Network must have a Subnet named as AzureBastionSubnet
- The AzureBastionSubnet must be at least /27 or larger
- Azure Bastion uses a Public IP and it must be a Standard Public IP SKU
To use Azure Bastion
- Any HTML5 browser
- Users or Security Groups who will use Azure Bastion feature must have
- Reader role on the Virtual Machine(s)
- Reader role on the NIC with private IP of the Virtual Machine
- Reader role on the Azure Bastion resource
Provisioning Azure Bastion in a fresh environment
Create Azure Bastion
First, let’s create Azure Bastion Resource by typing at Azure Search Bastion and click Bastions

At the Bastions, click Add
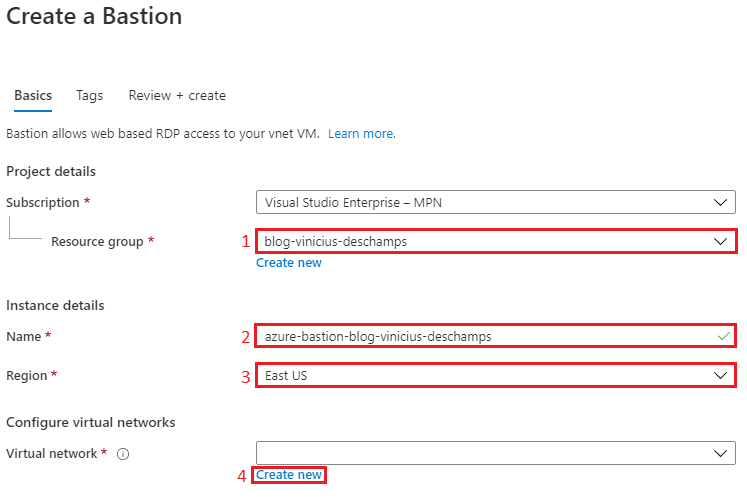
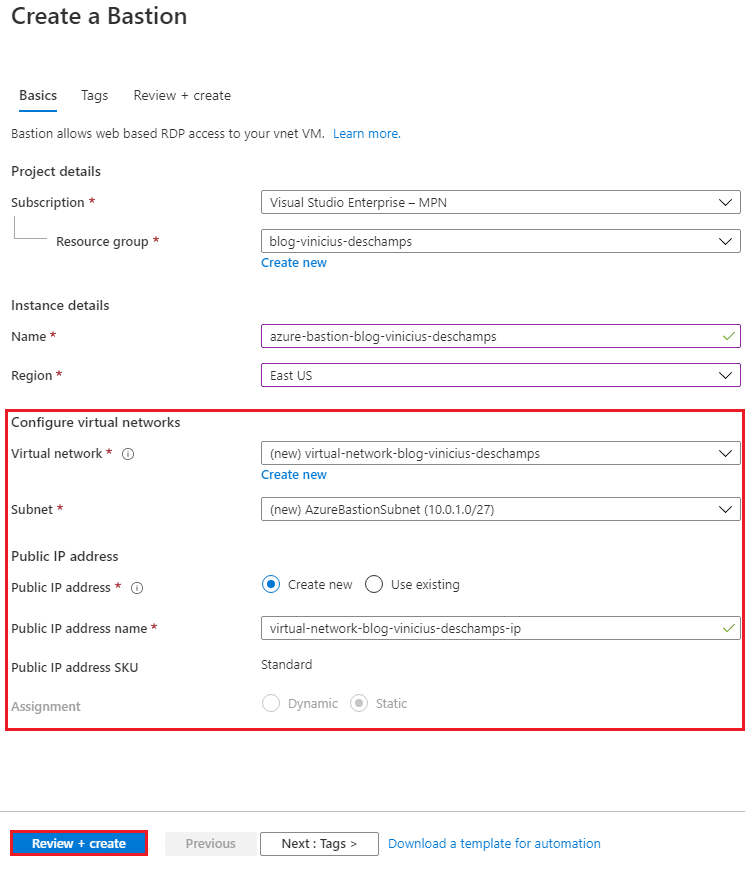
To create a Bastion, choose a Resource group (1), a Name (2) for your Bastion instance as well as the Region (3), then click Create new (4) to configure a new Virtual Network
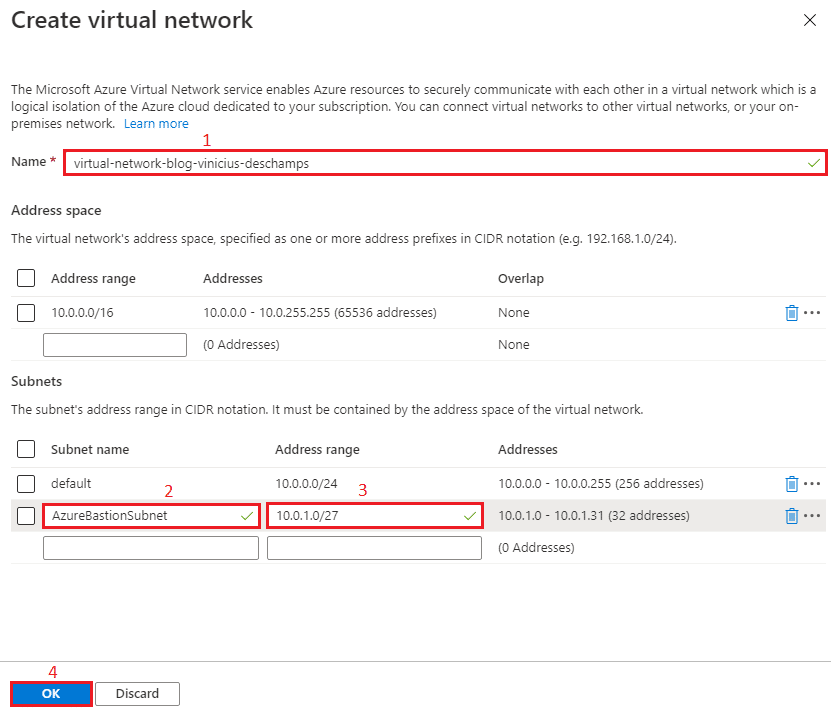
While creating a virtual network, please keep in mind that your Azure Bastion must have a subnet named AzureBastionSubnet, its Address range should be at least /27 and address space should be able to accomodate it.
Once you create the new Virtual Network everything else under Configure virtual networks is filled but feel free to change if you have a specific need to create the Bastion resource. Then press Review + Create
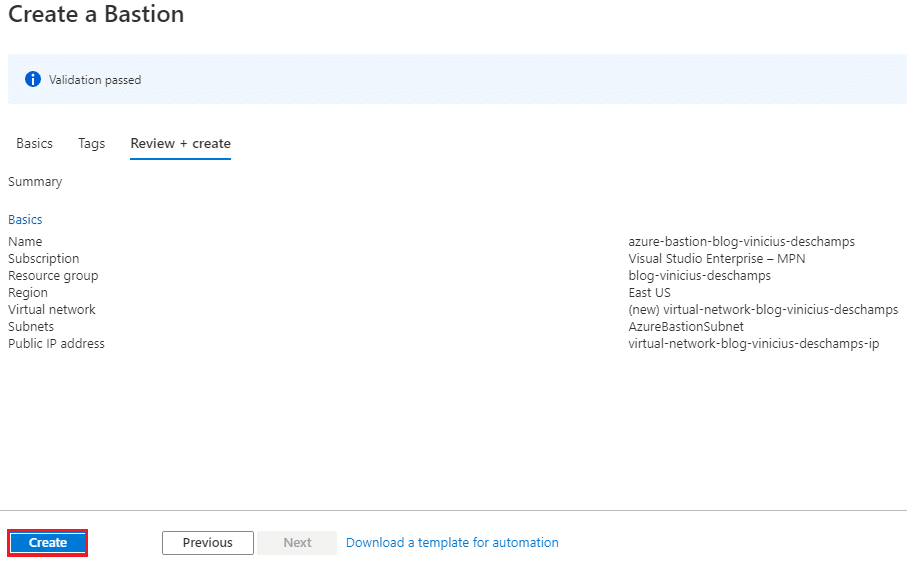
Now, double check that everything is ok and click Create
Create a Virtual Machine with Bastion
Type at Azure Search Virtual Machines, and click Virtual machines

In Virtual Machines, click Add (1) and Virtual Machine (2)
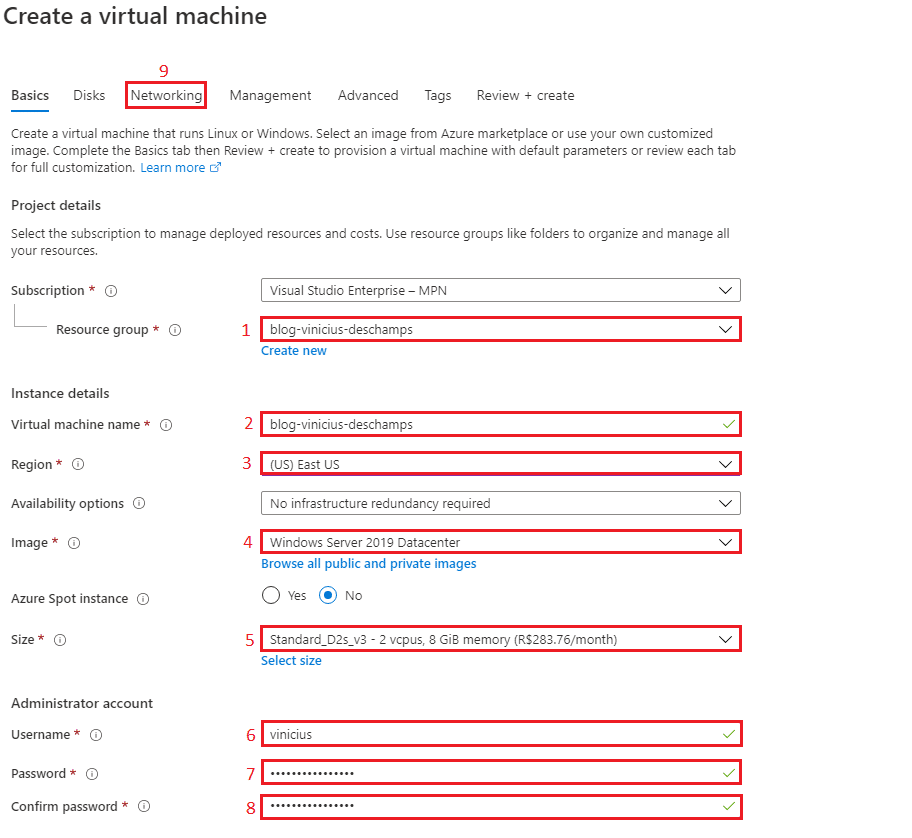
You will have to provide all the information from 1 to 8 and then click in the Networking tab
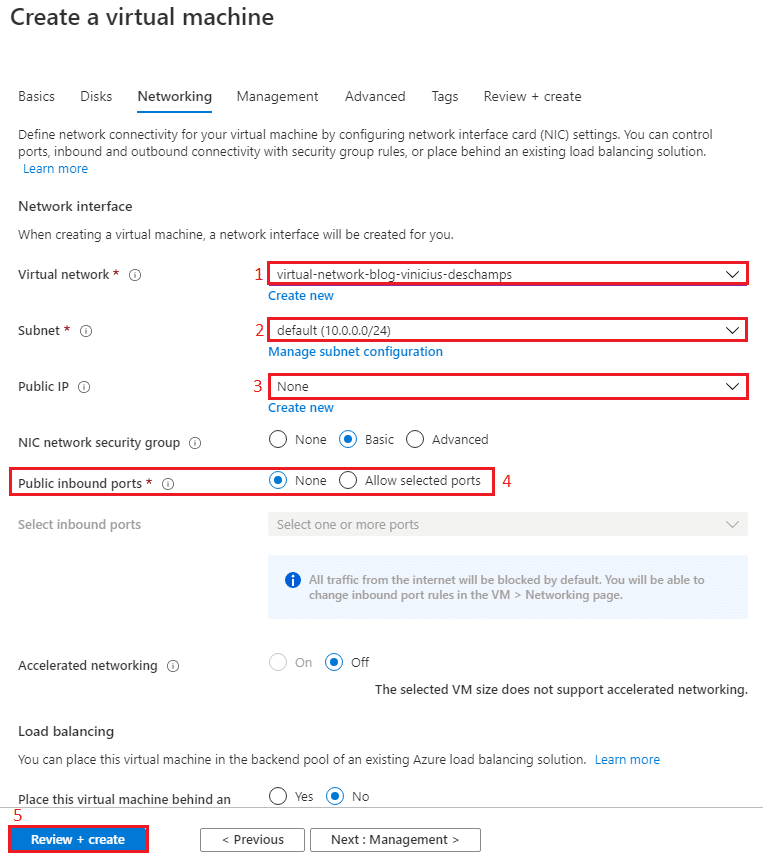
In Networking you should be careful to choose the options and ensure you are selecting the same Virtual Network (1) you used to create the AzureBastionSubnet, and choose any Subnet (2) available.
Please note that I choose None for the Public IP (3) and Public inbound ports (4) because Azure Bastion does not require that the Virtual Machine has a Public IP since we are going to connect via Azure Portal
Then click Review + Create
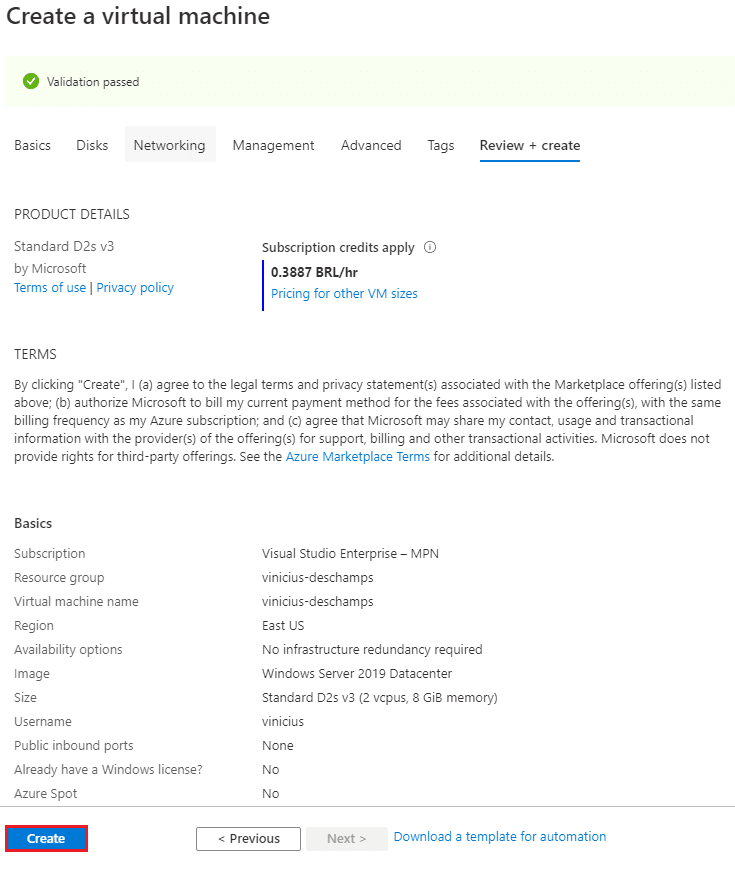
Double check your Virtual Machine, and click Create
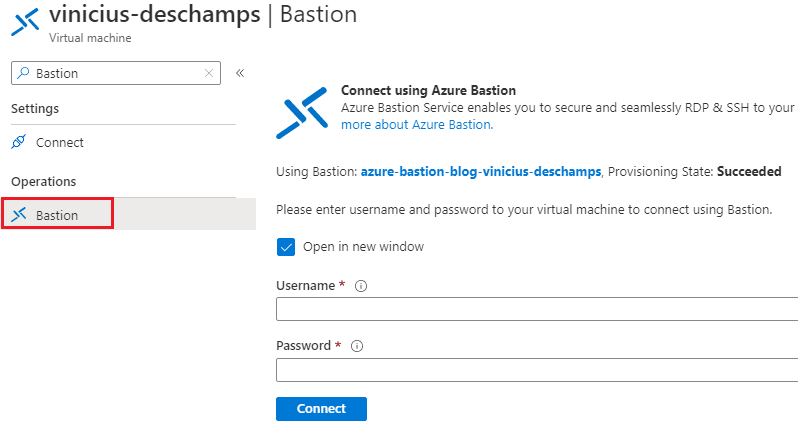
Connecting to the Virtual Machine via Bastion
Go to the Virtual Machine you just created, and search for Bastion
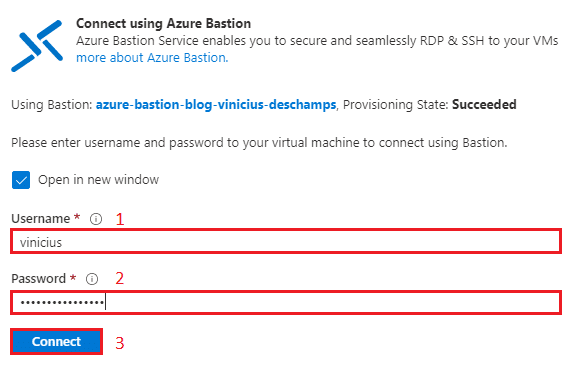
In the Connect using Azure Bastion, provide your Username (1) and Password (2), then click Connect (3)
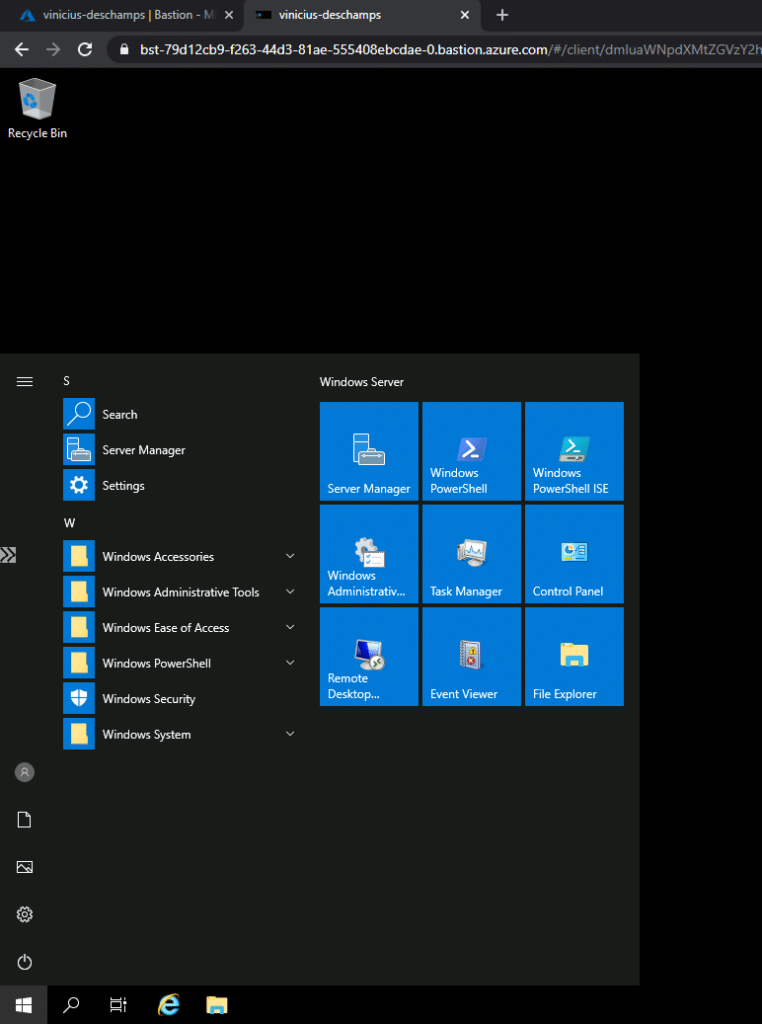
And voilá, you are now accessing your Virtual Machine through your browser
I hope you liked it
And I’ll see you on my next post
Photo by James Sutton on Unsplash
