On my previous post, I’ve guided you through the steps you need to take in order to add license.xml into the Data folder based on Sitecore recommendations, which means provisioning /Data folder outside of /Website root folder.
That being said, what you are not aware since my last post, despite it was a straight forward change for fix – let’s say easy – issue that you wouldn’t imagine by following Sitecore documents you were in fact hardening your Sitecore installation!
“Wow! Are you serious?” Yeah, you can bet on it! So, if you hadn’t have chance to check what I am saying right now, I would encourage you to read my Sitecore installations – tips and tricks #2
Alright, ladies and gentleman, moving forward… So, as you probably know hardening reduces the attack surface by disabling functionality that is not required while maintaining the minimum functionality that is required.
“Wait a minute! Are you saying that my Sitecore will run at its minimum capability????” No, no at all!
Let’s assume that you have a gate on your house, would you leave it open all day long? So, anyone could simple jump into? So, the idea behind hardening definition works on the same way, which means if you give a remote to open the gate just for the people allowed to jump into and keep it closed, will your gate works at its minimum capability? No, no at all! By giving a remote for strict people, you have created an “Access Authorization Control” in order words, you have hardened your gate!!! (yay!)
Now, let’s back to business 🙂
“Sitecore recommends that you follow all the security hardening instructions described in their documentation”
On today’s post, I’ll walk you through in how to deny anonymous access to Sitecore key folders, which are:
- /App_Config
- /sitecore/admin
- /sitecore/debug
- /sitecore/shell/WebService
So, open Internet Information Services (IIS) Manager and navigate to Sites, Sitecore Instance (e.g. MySitecore) and expand it
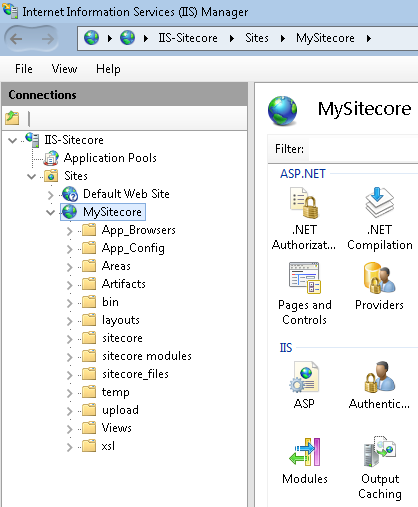
Now, have a look and find all folders listed above.
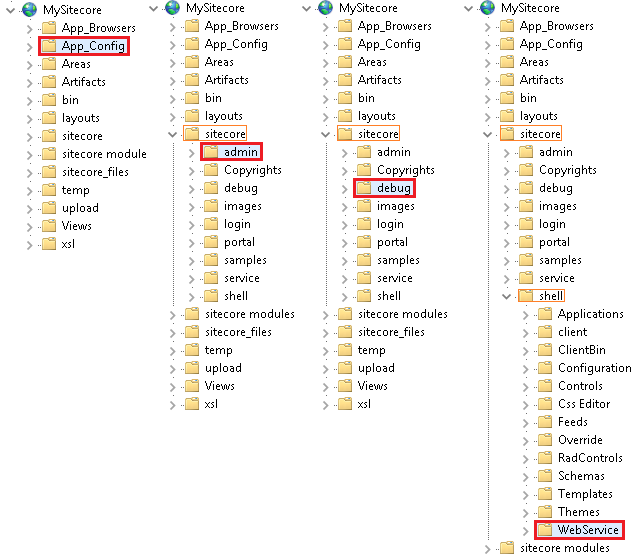
Alright, everything is where it should be, isn’t it? GOOD, moving on….
Important: I would recommend to check if your Sitecore instance is up and running before follow the steps below
1. Back to the root of Sitecore Instance, in my case here MySitecore, and expand it
2. Let’s go through folder by folder and DENY anonymous access on it
3. Find App_Config and select it
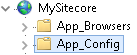
4. Once App_Config is selected, have a look at your right and you’ll notice an Authentication icon (double-click)
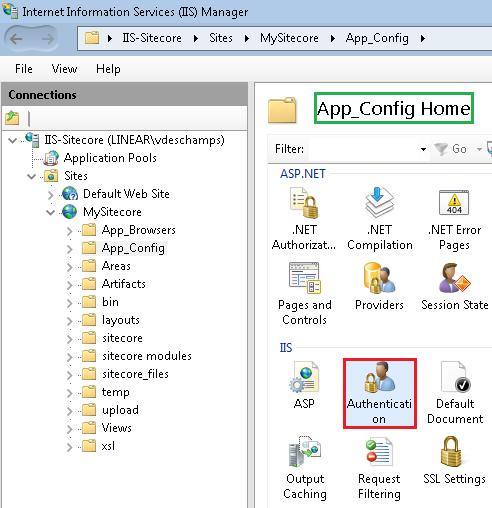
Important: As you can see App_Config Home is highlighted in green color, which tell us the changes will be applied from this level (App_Config) to all child items. In other words, we are breaking the inheritance to this folder.
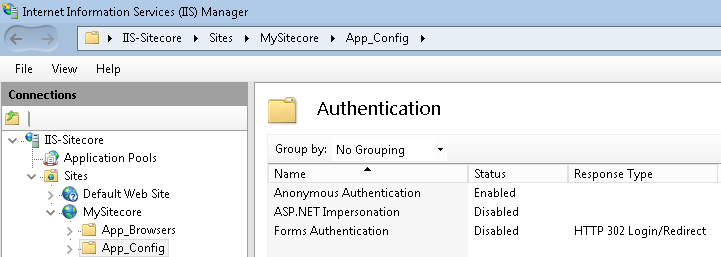
5. In the Authentication folder, you’ll see all authentication methods available on your Web Server
6. Find the Anonymous Authentication, click on it and in the Actions panel at your right click Disable
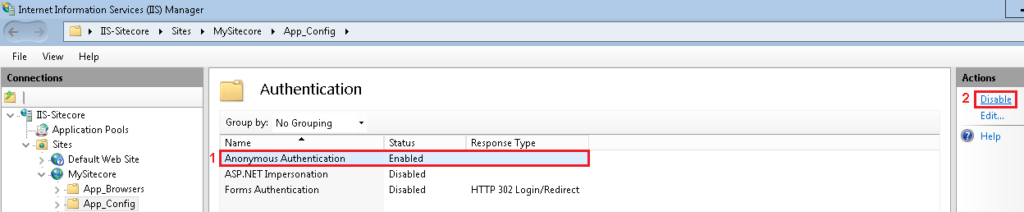
7. Once you disable the Anonymous Authentication for App_Config, at your left click on Your-Server-Name, in my case IIS-Sitecore, in the Connection Home Panel
8. Now, with IIS-Sitecore selected, in the Actions panel at your right click Restart
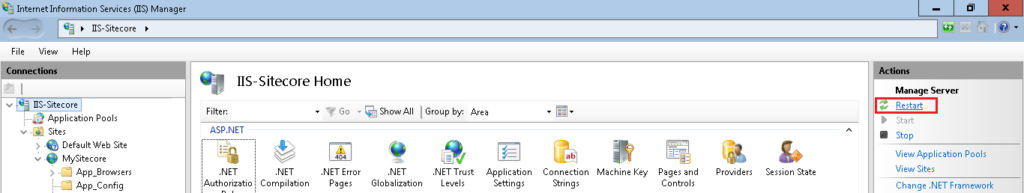
“That’s it? Is it working?” Your call, let’s test it….
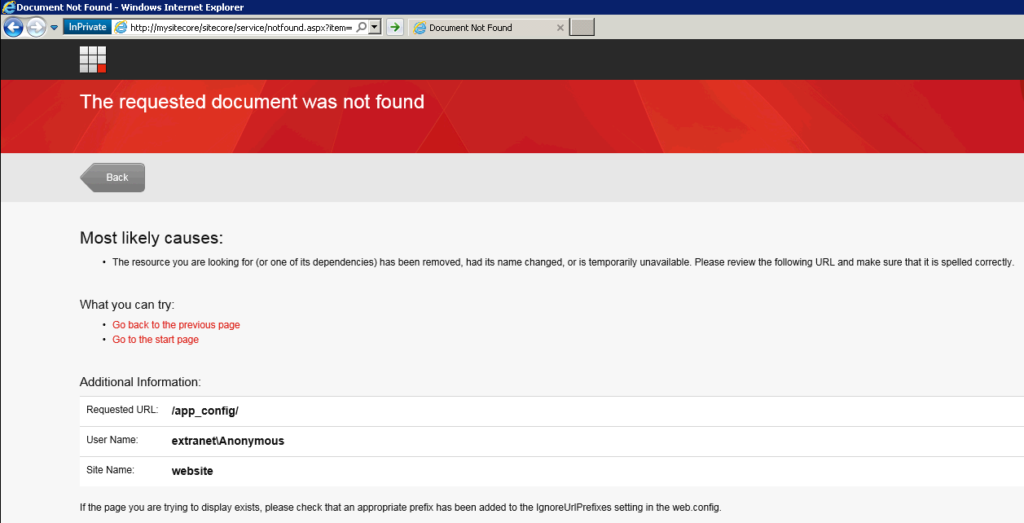
“YAY! IT WORKS!” Well, not so fast buddy – SORRY! As you can see, it is a Sitecore 404 custom page. I would say, fair enough because we don’t have any ASPX file inside and even if you have tried before the whole process you would notice that this page still shows up!
“WHAT?!?! Why should I deny Anonymous Access if Sitecore already throws a 404 page that protects me?”
The App_Config folder contains a lot of very important configuration files from your Sitecore instance that could have privacy concern. Also, let’s imagine you have a readable file, like a TXT, inside of App_Config called ConnectionStrings.config.backup.TXT and call the full Sitecore path on the browser.
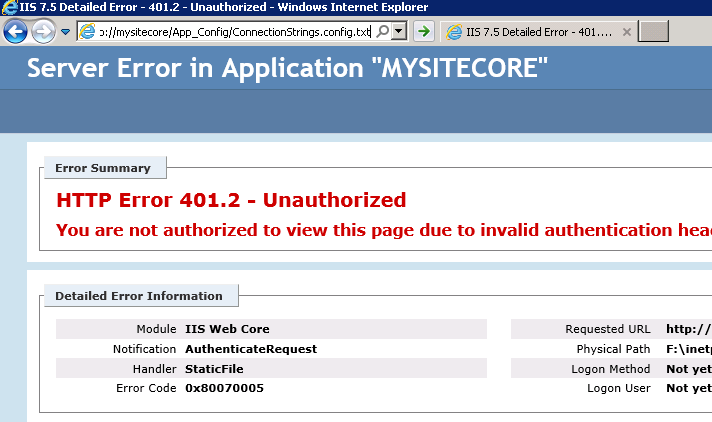
WOW! Are you glad that you have followed Sitecore recommendantions, aren’t you? Can you imagine your ConnectionStrings’ backup file exposed?
Despite Sitecore on its default installation avoid anonymous access to the folders installations by throwing the error “The requested document was not found”, this won’t guarantee your privacy content has an extra security layer.
Now, that you have completed, tested and had the result of your modification for /App_Config, you will have to repeat the steps 1-8 for the remain key folders: /sitecore/admin, /sitecore/debug and /sitecore/shell/WebService
Still with me? Cool! Keep in mind the steps listed on this post are recommended to all Sitecore instances, no matter which role they are going to play!
That’s it! Thanks for reading and I’ll see you on my next post!
