One of the most exciting – and easy – things to perform now with Sitecore Identity is the integration with Azure Active Directory (AD) which allows your users authenticate with the same credentials as for their corporate email.
Last September, I had the opportunity to set up an integration by following Derek Correia’s blog. So, I’d asssume you now know how the process of integrating Azure AD and Sitecore Identity Server works.
The authentication and authorization happens through Azure AD Security Group because we configured the App Registration Manifest to use SecurityGroup at groupMembershipClaims, and for the Sitecore Role claiming flow is based on the Security Group Object ID set at Sitecore.Plugin.IdentityProvider.AzureAd.xml file along with the role it should request.
Once you have configured the integration, you will notice users are now able to access Sitecore Content Management using their Azure AD credentials.
A couple weeks ago, I received a request saying a user was not able to sign-in using his Azure AD credentials and was seeing either HTTP ERROR 431 or a blank page with no further information.
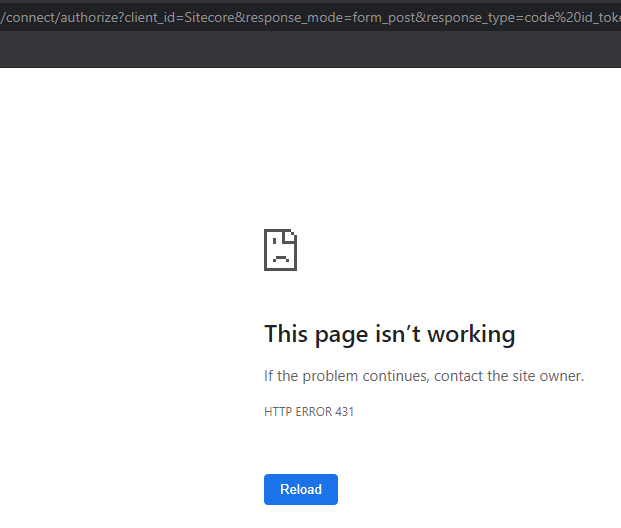
I’ve asked the user to test
- On his cellphone but not connect to the company wireless
- In a coworker’s computer
Nothing worked, so I started to think it might be something with his profile on Azure AD. So, I’ve compared our accounts and the biggest difference was the number of Azure AD groups we belong to.
The user is member of 180 groups
Then, in order to validate this, I’ve added myself to the same groups and I was able to reproduce the error.
I decided to open a Sitecore ticket, explained the situation, shared logs and they come up with a possible solution but unfortunately didn’t work
Please consider applying the fixes suggested in the sample code below to your Identity Server and to all the loadbalancer/gateway/network infrastructure you put in place in front of Identity Server:
<system.web>
…..
<httpRuntime maxRequestLength=”2097152″ />
</system.web>
While Sitecore was investigating, I continued the investigation and tried to find the following answers
- Is Sitecore looking just for the groups listed in the Sitecore.Plugin.IdentityProvider.AzureAd.xml file?
- Does it matter if the group is a Security or a Distribution group?
- What’s the maximum of groups I can be member of and sign-in with no issues?
Is Sitecore looking just for the groups listed in the Sitecore.Plugin.IdentityProvider.AzureAd.xml file?
Please feel free to correct if I am wrong here but on my understading, during the authetication process all the membership is conveyed from Azure AD to Sitecore, and validated at the Sitecore.Plugin.IdentityProvider.AzureAd.xml. In summary, it does not matter if you have a single or a 1000 claims, what will matter is how many groups you belong to.
Does it matter if the group is a Security or a Distribution group?
As mentioned earlier, as the App Registration Manifest is set to use SecurityGroup at groupMembershipClaims the only group type that is being consider are the Security Groups
What’s the maximum of groups I can be member of and sign-in with no issues?
The only way I could determine was doing by trial and error
- Check # of groups I am member
- Remove from groups individually
- Test again
There’s a way to check the Group Membership through Azure Portal, however, it gives you the total and not just the Security Groups, so I had to use Powershell
$FindUser = “[email protected]”
(Get-AzureADUser -SearchString $FindUser | Get-AzureADUserMembership -All $true | ? {$_.ObjectType -ne “Role”} | % {Get-AzureADGroup -ObjectId $_.ObjectId | select DisplayName,ObjectType,MailEnabled,SecurityEnabled,ObjectId} | ? {$_.SecurityEnabled -eq $true}).count
Here is the expected output (please note the time may vary depending on the # of groups you are part of)
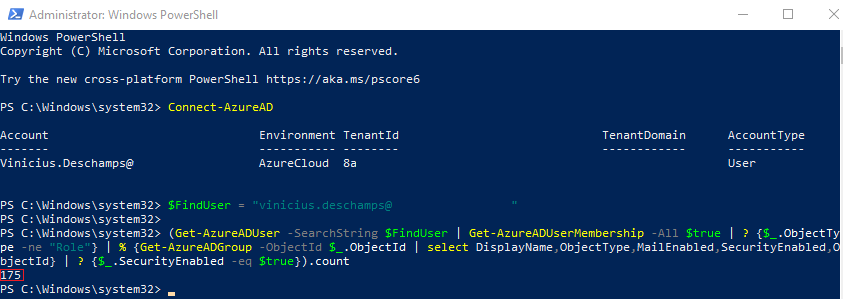
Note that the total of Security Groups is 175, and I am receiving either the HTTP Error 431 or blank page, so it’s time to test and find out the magic number!
1st attempt
Reduced to 150 Security Groups, and the error went away
2nd attempt
Increase 10 Security Groups, 160 in total and still NO ERRORS
3rd attempt
+10 Security Groups, and still NO ERRORS
So, fingers crossed I might have something now…
4th attempt
Now, +1 Security Group and BAM! THE ERROR IS BACK UP
170 is the magic number we were looking for
Why 170? What is causing this limitation?
Sitecore Support asked for a Fiddler Trace to perform further analysis and they back up saying the following
“I tested that the limit for the cookies is around 32KB and your request – while having 175 groups – was around 34KB”
In addition to that, Sitecore support said
To workaround this Azure limitation you could
- Decrease the number of groups of your users are in
- Move your Identity Provider from the App Service to a Windows Server VM where you have access to those registry keys
- increase the value of MaxFieldLength and MaxRequestBytes in the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\HTTP\Parameters registry
Once again, huge thanks to Sitecore Support
I hope you liked it, and I’ll see you on my next post!


Deixe um comentário