In today’s post, I am going to show you how to grant access to a Virtual Machine using Azure Bastion.
Azure Bastion highlights
As you probably saw in my Improve Security with Azure Bastion post, Azure Bastion is a PaaS service that provides a secure RDP and SSH connectivity to shield your Azure Virtual Machines.
That said, your virtual machines are no longer exposed through Internet when Azure Bastion is in place, therefore the access to them are made directly via Azure Portal.
Access Control (IAM)
At the same time you want to improve security, using Azure Bastion, you don’t want to wide open the Azure Portal access to the users who needs access to the VM, right?
In order to accomplish that, you should use Access Control (IAM) which is used to provide granular access to Azure Resources, and it is possible to cover Azure Bastion’s specific requirements as well.
Azure Bastion permissions
The permissions Azure Bastion requires at least are the following Reader roles
- On the Virtual Machine
- At NIC with private IP of the Virtual Machine
- The Azure Bastion resource
How to Grant Access to VM using Azure Bastion
Virtual Machine
Once you are at the Virtual Machines, pick the one you configured Azure Bastion, and click on it (1), choose Access control (IAM) (2), click Add (3) and Add role assignment (4)
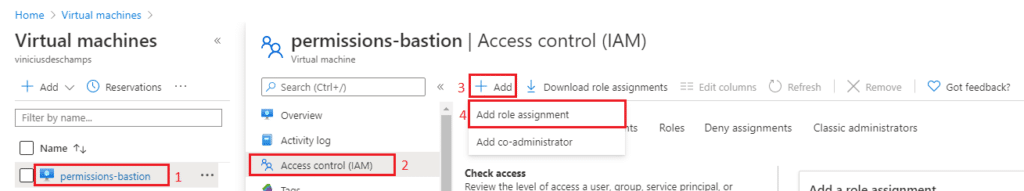
You will notice the following blade opened in your window, Add role assignment, please fill accordingly Role (1) choose Reader, type the name of the user you want to grant access in Select (2) field, and select it (3)
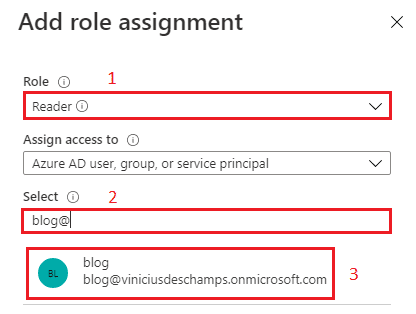
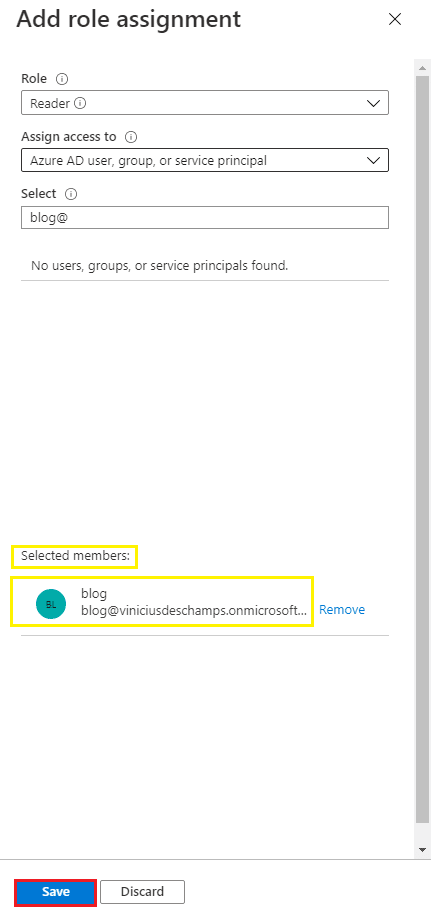
Once you select it, check the Selected members has the expected users and hit Save
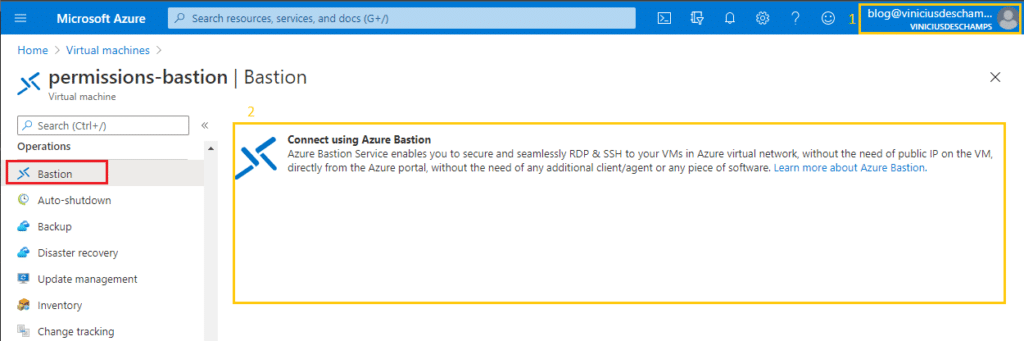
And as a side note, if you attempt to connect the user and have them to use Azure Bastion right after to provide Reader Role in the Virtual Machine this is how they will see the screen, no errors, nothing wrong but at the same time nothing to connect or provide credentials
NIC with private IP of the Virtual Machine
While still at the Virtual Machine (1), click on Networking (2), then on its Network interface (3)
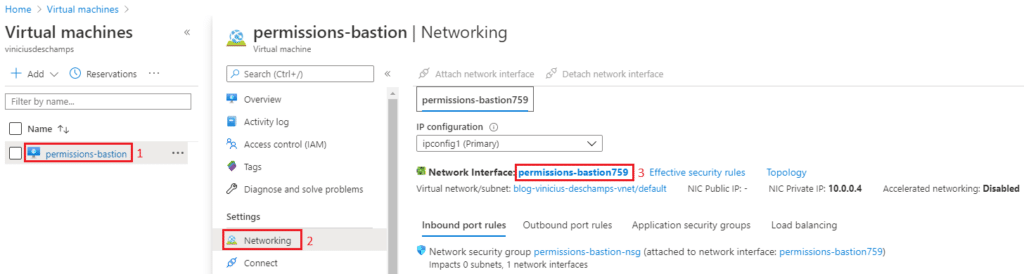
At the Network interface blade, click Access control (IAM) (1), Add (2) and finally Add role assignment (3)
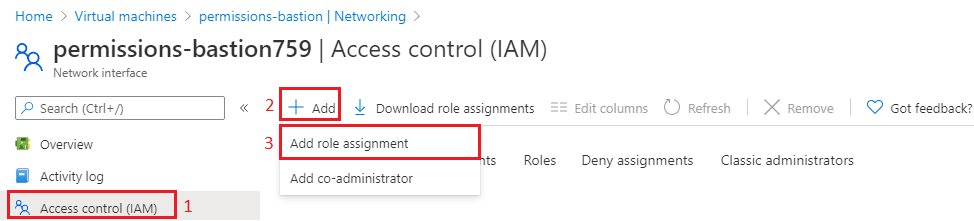
You will notice the following blade opened in your window, Add role assignment, please fill accordingly Role (1) choose Reader, type the name of the user you want to grant access in Select (2) field, and select it (3)

Once you select it, check the Selected members has the expected users and hit Save

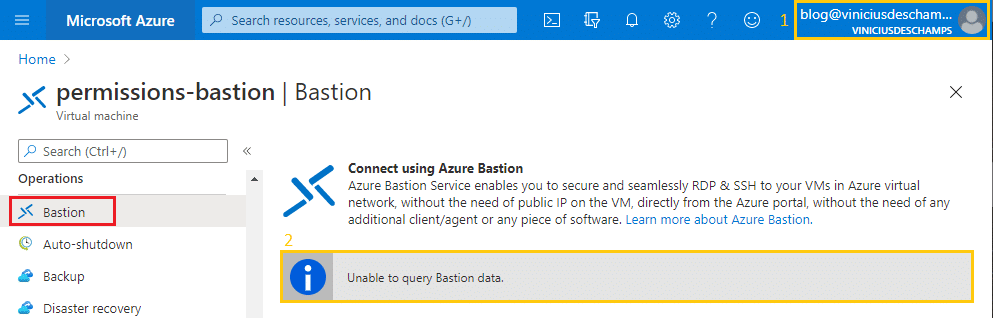
And if you try to connect right away with Azure Bastion, that’s how the screen will look like, please note that now there’s a message Unable to query Bastion data
Azure Bastion resource
Go to Azure Bastions in Azure Portal, and click at it (1), Access control (IAM) (2), Add (3), then Add role assignment (4)
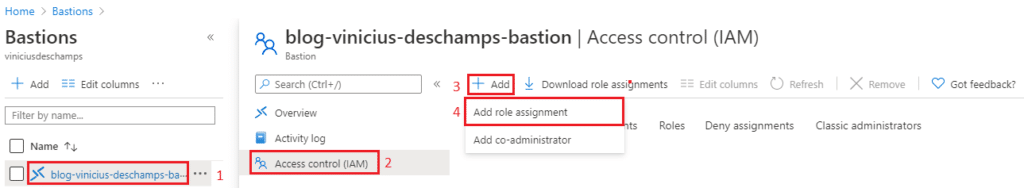
You will notice the following blade opened in your window, Add role assignment, please fill accordingly Role (1) choose Reader, type the name of the user you want to grant access in Select (2) field, and select it (3)

Once you select it, check the Selected members has the expected users and hit Save

And, voilá! You are now seeing Username, Password and Connect
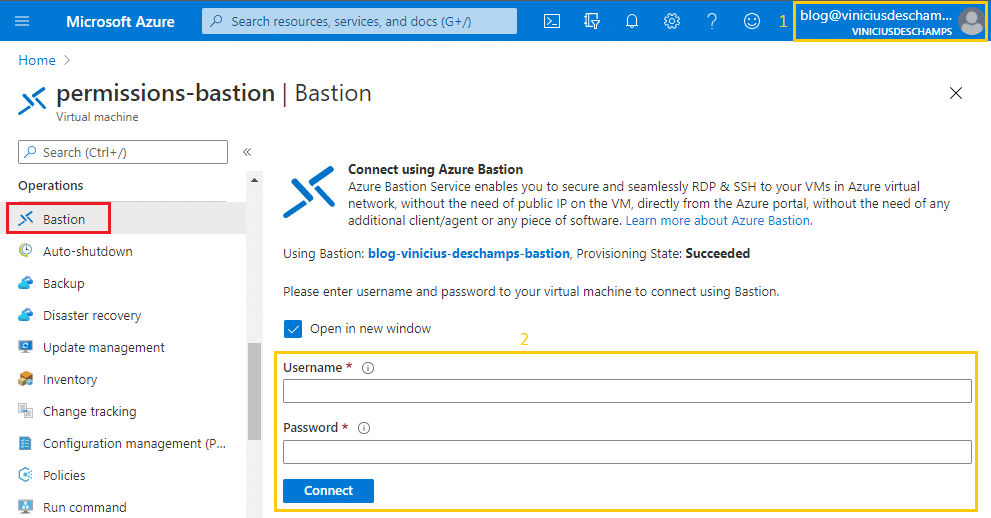
And that’s it
I hope you liked it, and I’ll see you on my next post
Photo by Clarissa Watson on Unsplash

1 comentário em “Grant access to Virtual Machine using Azure Bastion”